
ZoneRanger is the most complete solution for securely extending your trusted monitoring and observability infrastructure across disparate security boundaries while leveraging your existing investments.
In today’s business environment, knowing that your network management and monitoring traffic is protected throughout is a critical concern. The protocols, data and tools that are used to manage today’s complex IT environments expose organizations to more risk than they realize. ZoneRanger gives you secure management traffic protection across all zones of the network.
Designed to integrate seamlessly into your existing network infrastructure, ZoneRanger is compatible with ANY device and ANY application.

Why do companies choose ZoneRanger?
Improve Your Decision Making With Actionable Data Right At Your Fingertips
Improved Security Posture
Remove the risk of human error from firewall rule-based traffic validation. Creates a “Safe Sandbox” for operations teams to do what they need without impacting firewall governance
Increased visibility
Statistical Analysis brings a unique view to management traffic by visualizing aggregated traffic by its type, and the data received, processed, forwarded, and discarded, with the capability to drill down into the contributing traffic patterns by source and destination device, port, and protocol.
Time to value
Realize substantial savings by minimizing firewall rule changes, simplifying network address translation, significant reduction in IT operations tasks, and support compliance and audit missions
Better Event Distribution
Consolidate telemetry data and critical IT management traffic into easily managed pipelines that allow you to control how data is filtered, routed and consumed across your IT application landscape.
Simplify Network Management
Decrease the proliferation of management applications and application-specific probes and agents. Simplify managing networks with overlapping private IP addresses.
Pragmatic Security
Confidently deploy management applications across security boundaries – hybrid trust – zero trust networks. Provide IT organizations full transparency to management applications and end-devices without violating security policy.
Vendor Agnostic
ZoneRanger and Ranger Gateway communicate with your existing network management systems and IT assets. ZoneRanger is 100% transparent to management applications inside the operations center and the devices throughout your network . No application or device modifications are required to deploy ZoneRanger. Today there are Tavve customers using industry standard applications from Splunk, Datadog, Grafana, Elastic, SolarWinds, Nagios, ManageEngine, Zabbix, Cisco, Netcool, plus many in-house applications based on industry standard management protocols.
Managing IT assets across security boundaries
Because corporate security restricts many management related network protocols from traversing security boundaries as a matter of policy, IT management systems often cannot directly manage devices and applications across disparate security boundaries. ZoneRanger extends management capabilities to devices, networks, workloads and applications beyond trusted security boundaries. Each ZoneRanger provides communication across security boundaries via a Ranger Gateway, using a secure 128-bit encrypted session.
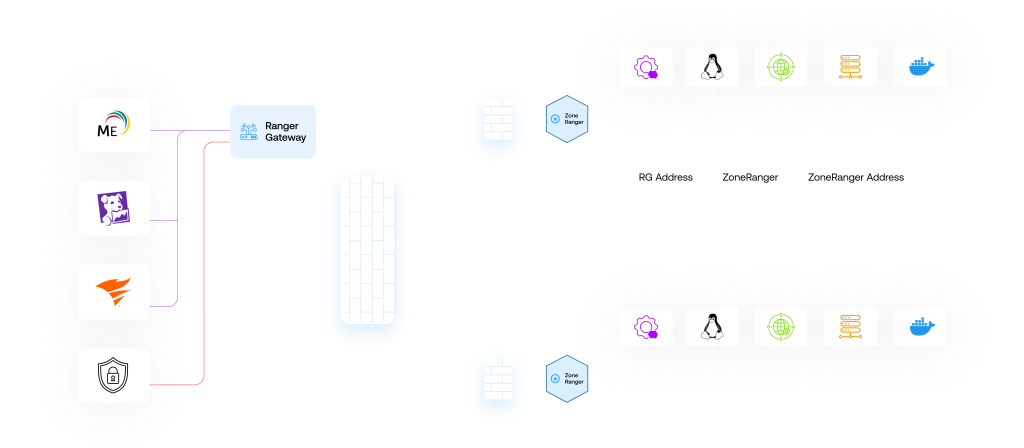
Managing Overlapping IP Addresses
Overlapping IP address ranges have become major obstacles to effective network management. ZoneRanger resolves the overlapping address problem by proxying management data to the managed devices. ZoneRanger needs to have only a NAT address. Traffic is proxied by ZoneRanger (with Ranger Gateway) to the desired overlapping IP address. Existing network management systems, which cannot reach devices because of overlapping IP networks, which would typically rely on one-to-one NATing inside the firewall, are now able to communicate to any device through the ZoneRanger and Ranger Gateway.
Say “YES” to UDP and other restricted network protocols
Due to security, most organizations restrict UDP traffic from passing beyond the security boundary. ZoneRanger filters and securely passes data from restricted network protocols, such as SNMP traps, NetFlow/sFlow, ICMP or Syslog. This feature is applicable to any network protocol that may be restricted from passing across security boundaries. ZoneRanger establishes source-based rules to forward messages to the correct destination(s). For example, ZoneRanger blocks unauthorized SNMP traps while acceptable traps are consolidated, filtered, inspected, verified and delivered to multiple destinations.


More to Do With Limited Staff
IT organizations are tasked with managing and supporting larger, more complex networks with smaller teams. Security teams are tasked with a never-ending effort to ensure the correct data and information is available, and the threat risk is minimized. ZoneRanger is a unique and unparalleled solution for managing difficult to reach areas of a network. It eliminates 95% of firewall rules associated with IT operations communication, and at the same time, gives IT operations greater visibility to devices and information. The personnel impact of the typical ZoneRanger deployment has an ROI of less than six months. This massive reduction in labor allows the limited technical resources to be deployed on other tasks instead of hiring additional staff or putting needed projects on hold.
Firewall Rule Changes -- Death by Committee
The impact of changing a firewall rule or opening another port on the firewall is a complicated process to evaluate the risk exposure of the firewall change. ZoneRanger eliminates the need for multiple rules and ports. Adding or removing a device or application does not require a firewall rule change.
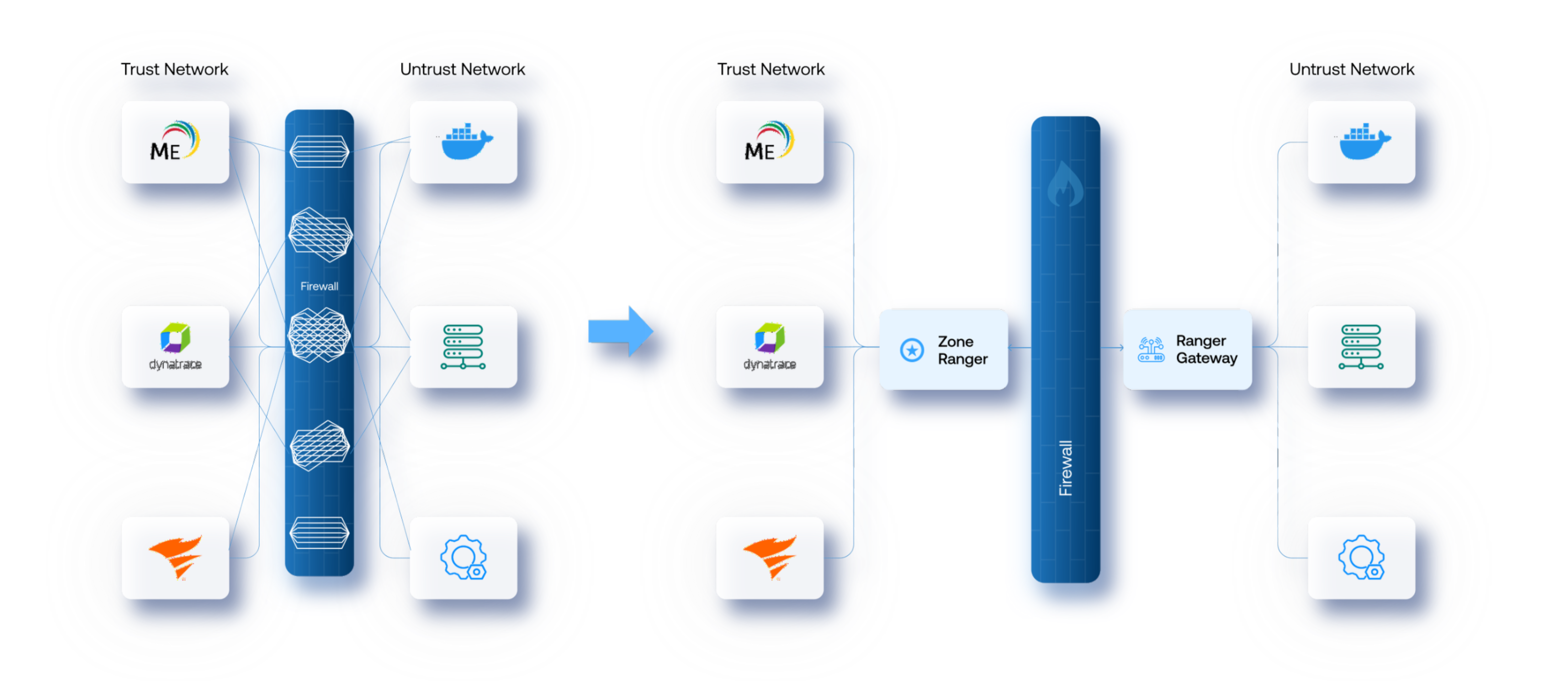
Confidently extend your trusted operations environment beyond security boundaries
Try any of Tavve’s solutions for free, or get in touch with an expert for a custom demo.
- 14-day free trial
- No credit card required
- Cancel anytime